Researchers have succeeded in developing an attack that can identify anonymous visitors to a website. The technique, which bypasses all the protections put in place by browsers, can be launched without the Internet user realizing that his identity has been exposed.
 |
| How to unmask anonymous Internet users |
There are many tools to protect your privacy on the web, such as VPNs to hide your IP address . The Tor browser , for example, uses a decentralized network and even goes so far as to impose a window size on opening to prevent sites from using the dimensions to identify a computer. However, even with all these precautions, it is not always possible to protect your privacy .
Researchers from the New Jersey Institute of Technology , in the United States, have discovered a method that makes it possible to identify Internet users through their profiles on major platforms and social networks . Concretely, it is not a question of discovering the identity of a lambda Internet user, but of confirming the visit of someone whose account is already known.
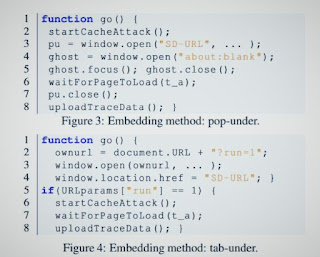 |
| Sample code to launch the attack in a background window or tab. © New Jersey Institute of Technology |
The attack relies on sharing content from major platforms
To get started, it is necessary to own a website. This could be a site run by hackers, or for example an anonymous forum that law enforcement has taken over.
This attack is somewhat devious, and is based entirely on selective content sharing functions of sites like Facebook, Twitter, TikTok , but also YouTube and Dropbox and many others. Site managers must therefore have a list of suspects, of whom they know at least one online account.
The attack consists in creating a publication, either limited to one or more people in this list, or public but prohibited to these same people. It works both ways. All they have to do is share the post on their site.
Browsers have safeguards in place to prevent the site owner from knowing whether visitors have been able to view the content. However, and this is the central point of this attack, they can have information about the operation of the cache memory of the processor.
 |
| Operation of the Leakuidator+ extension which protects against this kind of attack. © New Jersey Institute of Technology |
An attack that uses CPU cache access time
Sites cannot see the contents of other sites' cache memory, but this memory is limited and requested by all processors. By loading content that requires a lot of cache memory, they can measure the execution time. Using machine learning, they can then identify the delay produced when other specific content competes for that cache. This allows them to infer whether or not the browser was able to load the post. So if the user opened a file on Dropbox that was only shared with one account, they can confirm their identity.
This type of attack can hardly be launched en masse and presents little risk for the majority of Internet users. However, the technique could be a way for governments to monitor the online activity of activists and journalists, political opponents or even minorities. And there's no way to know if his identity has been exposed. Pending a possible fix in browsers, researchers have released the Leakuidator+ extension on Google Chrome and Mozilla Firefox, which warns the user of a suspicious request and gives them the choice to display the content or not.
Add Comments